Oh, dear, I reckon you want to know about this thing called “Matrix Attack.” Now, I ain’t no expert, but I heard folks talk about it and tried to make some sense of it for ya. So, sit tight, and I’ll tell ya what I picked up.
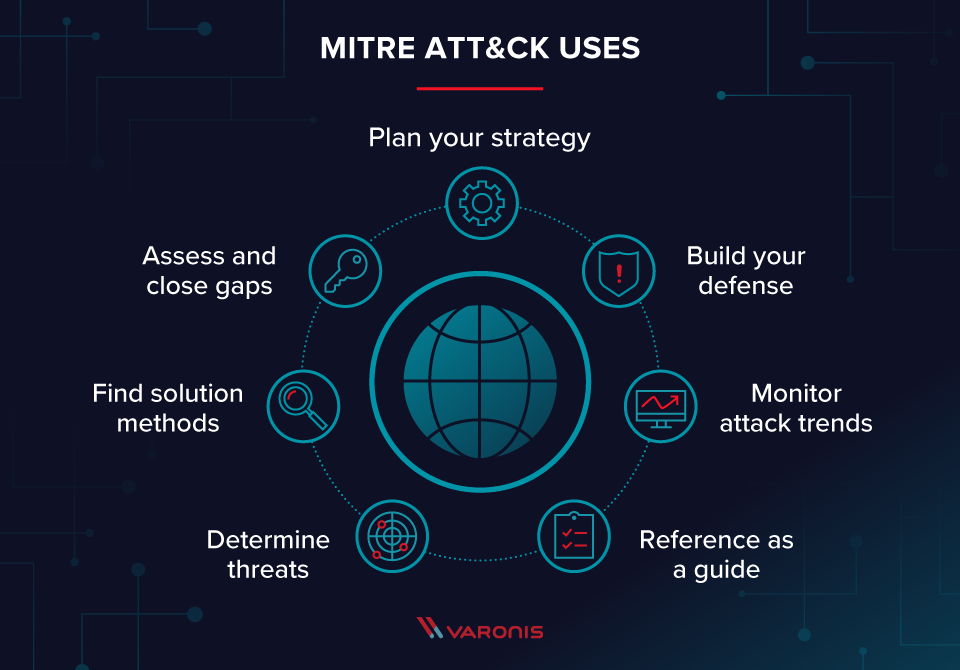
Now, “Matrix Attack” ain’t somethin’ that’s got much to do with them movies where people get all tangled up in the Matrix. This one’s about somethin’ called the MITRE ATT&CK framework. Folks in the cyber world, they use this here framework to keep track of all the dirty tricks that hackers use when they wanna cause some trouble.
So, let me start with the basics. You know how a matrix is like a big grid, right? Well, in this case, it’s a big ol’ map of all the different ways a hacker might try to break into a system or steal some information. There’s a bunch of fancy words they use, like tactics, techniques, and procedures (TTPs), but don’t let that scare ya. What they really mean is just different ways hackers do their thing. For example, one hacker might try to sneak in through a phishing email, while another might try to trick the system by exploiting a weakness in the software.
The MITRE ATT&CK has different sections, or matrices, for different kinds of attacks. There’s one for regular computers, one for mobile devices like your smartphone, and even one for industrial systems, like them big machines in factories. Each of these matrices is like a big list that shows all the dirty deeds that can be done to cause harm. You can imagine it like a big ol’ recipe book for hackers, tellin’ ’em exactly how to cook up a mess.
Now, let me tell you about the cloud platforms. Some folks, they think the cloud’s all safe and sound, like a nice, fluffy sky up there. But hackers, well, they’ve figured out ways to get into the cloud too. Whether it’s a service like Office Suite or some fancy Identity Provider, they’ve got tricks to bypass all the security. This is where the “Matrix Attack” comes into play, showing how they might attack different parts of the cloud environment. The hackers might try all sorts of things to break in, steal data, or mess with the cloud services. It’s like they’re lookin’ for weak spots to stick their hands in and grab what they can.
Then there’s something called the ATT&CK Navigator. Now, this ain’t a tool for the average person, but it’s a handy thing for them folks who work in cybersecurity. It’s a tool that helps them see which parts of the Matrix have been covered, and where they might need to do more to protect things. It’s kinda like when you’re watchin’ a hawk keep its eye on a henhouse—tryin’ to make sure no sneaky fox gets in. The Navigator helps ’em plan out defense strategies, so they’re ready for anything the hackers throw at ’em.
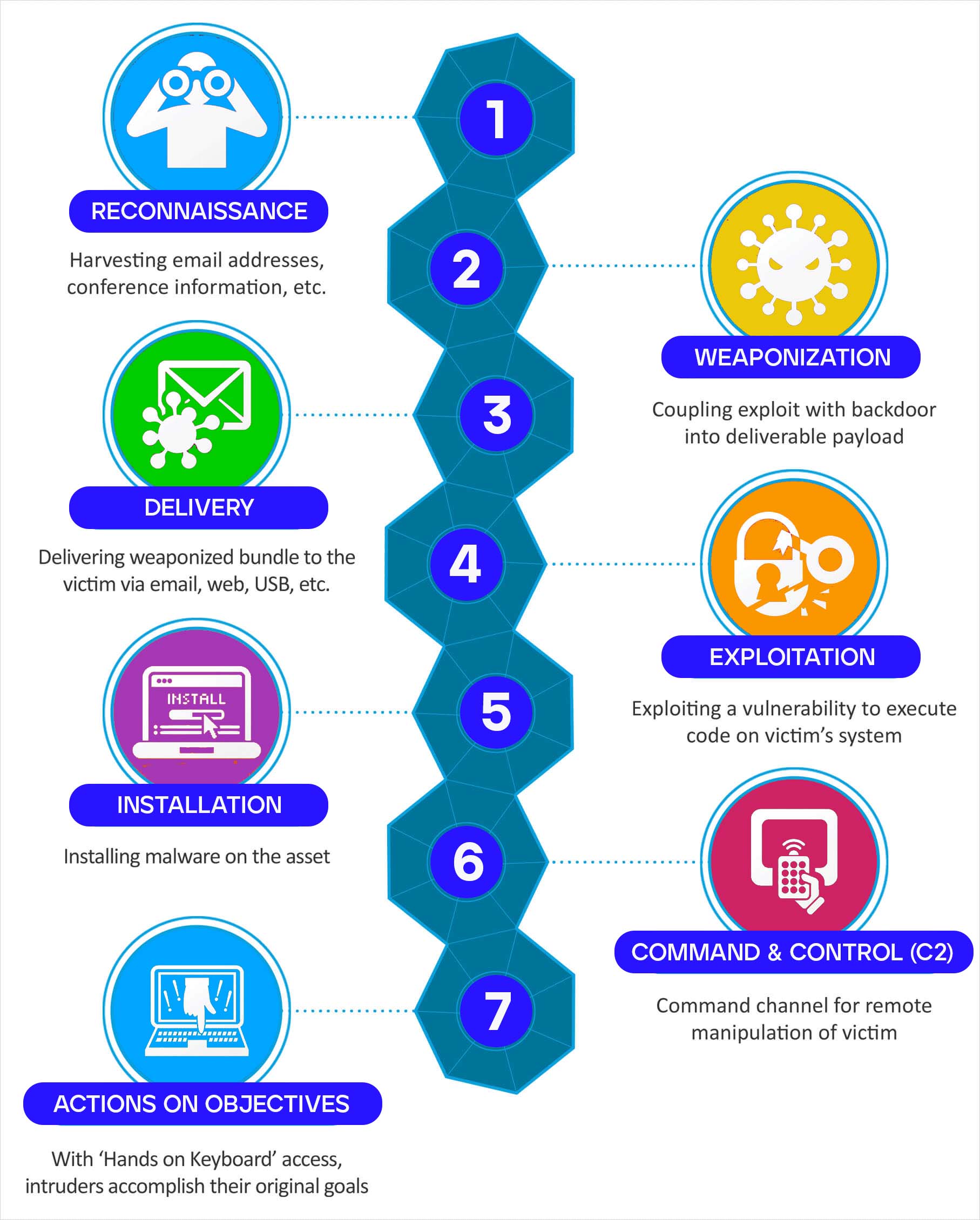
Let’s not forget the mobile devices, though. Now, people keep their whole lives on these little phones—pictures, messages, bank info, you name it. And hackers? Well, they know that if they can break into your phone, they can pretty much get their hands on everything. The Mobile ATT&CK Matrix helps to understand how hackers go after them phones, using tactics like network sniffin’, tryin’ to escalate their privileges, or even snatchin’ data straight outta the device. So, this here matrix shows how these dirty tricks unfold, step by step.
And, oh! I almost forgot about the industrial control systems. Some people might think that the machines in factories or power plants are safe, but hackers can be just as sneaky in those places. The ICS Matrix shows how hackers might try to mess with the machines that run things like power grids, water systems, or even transportation networks. They could try to sabotage whole systems, and if they succeed, it could cause a real mess for folks like us.
But here’s the thing—this ain’t all doom and gloom. The whole point of this Matrix business is so that them cybersecurity folks can learn the tricks hackers use and make sure they’re ready to stop ‘em. It’s a way to stay one step ahead of the bad guys. It’s like they’re playin’ chess, while the hackers are playin’ checkers. They’re thinkin’ ahead, so they can keep us safe.
All these matrices and tools, they might sound mighty complicated, but the important part is that they help protect what we care about. So, if you ever hear someone talkin’ about the Matrix Attack or MITRE ATT&CK, just remember it’s a fancy way of sayin’ folks are tryin’ to keep the hackers at bay and protect our lives, both online and offline.
Well, there ya have it. I hope I didn’t go and make your head spin with all these big words and fancy terms. But at the end of the day, it’s all about stayin’ safe, whether you’re usin’ a computer, a phone, or even a big ol’ factory machine.

Tags:[MITRE ATT&CK, Cybersecurity, Matrix Attack, Cloud Security, Mobile Security, Industrial Control Systems, TTPs, Cyber Defense, Cloud Platforms, Network Security]













